The Internet and Identity
mhrsntrk / July 15, 2022
Last year, it was an eye-opening experience for me to start working on Self-Sovereign Identity field. Currently, I am managing the Identity and Access Management product in Energy Web, and it gives me lots of insights on the concept and real-world use-cases.
Let's start from the beginning, I mean the creation of the internet! The task was very simple, just connect some number of computers which are far away from each other. But, we find more use-cases for the internet as it grows; such as online shopping, online banking, social media, etc. and all of these new use-cases is related to you as a user not the machine. But, the problem with the internet, it doesn't have a native identity and trust system, what it has is an IP/MAC address to identify your connected machine but not the person who is using it. In web2, we have two identity models to provide the identity system; Centralized Identity Model and Federated Identity Model.
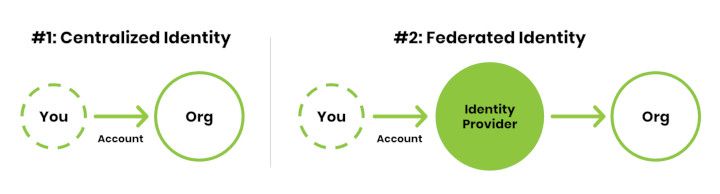
Centralized Identity Model
This is the most common model which is used by many applications today. You have a username/identifier on the application's database and in order to let the application know you own this username/identifier, you enter a user-generated password. So this is the username/password that we use every single day. So, I might hear you saying, what is wrong with this approach. There are two issues that you cannot solve by using a password manager;
-
Your data is siloed inside this application, so it is not portable or re-usable. You have to create an account for every application that you decide to use.
-
The centralized database which stores the user information is a potential honeypot for the hackers. Have I mentioned that global cybercrime damages are predicted to cost $6.000.000.0000.0000 (it is six trillion US Dollars, and yes it has that many zeros) annually by 2021?
Federated Identity Model
It is a fairly new concept for identity management, and the idea behind it was to solve portability and re-usability problems of the Centralized Identity Model.
In this model, we add an identity provider in the middle of user and application. You can easily recognize this model when you see “Login in with some_evil_company_name_here ”. In theory, you can use your some_evil_company_name_here to log in to services that have an integration. So does this model solve all of our problems? Of course not, it just creates a bigger honeypot for hackers.